Getting Visitor Management Right

Approach visitor management correctly and keep costs low
Monday morning, standing in front of the reception desk are a tradesman with a toolbox and a job applicant nervously glancing at his watch. Behind the desk, a substitute employee is leafing through a paper list and trying to figure out what to do on the phone. This is still what visitor management looks like in many places today. In this article, you will learn how visitor management works, what the challenges are, and how the right software can make everything easier.
What is visitor management?
Visitor management refers to all measures associated with receiving, controlling, and tracking guests. This includes customers, applicants, partners, service providers, and sometimes temporary staff or temporary workers.
The requirements for visitor management are diverse:
- Security: Who is in the building? Who is allowed where? Who is responsible in an emergency? These questions can only be answered if visitor data is complete, up-to-date, and available across all locations.
- Internal processes: How does registration work, manually or digitally? Who informs the respective host?
- Data protection: How is personal data collected, stored, and deleted? This is not just a matter of legal requirements, but also of visitor trust.
- User experience: How does the guest feel when they arrive? Are they treated courteously and in an organized manner, or does it seem improvised? The reception is often the first real contact with an organization and shapes the impression.
Well-thought-out visitor management creates structure and contributes positively to the external image. Especially in larger companies, hotels, or government agencies, it becomes a task that can no longer be done on the side. Instead, it requires a great deal of organization.

Typical problems in visitor management
Visitor management is still sometimes carried out with a great deal of manual work. Guests sign in on paper lists, receive a badge from a drawer, and are directed from reception to the meeting room. However, this and similar processes have a number of disadvantages:
- Poor overview: It is often impossible to determine conclusively who is in the building or who has already left. An incorrect visitor list is a problem during audits, fire safety inspections, or evacuations if, in an emergency, no one can say who is currently in the building.
- Prone to errors in visitor registration: Handwritten entries are sometimes made under time pressure and are difficult to read, incomplete, or forgotten. This leads to queries, searching, and information gaps.
- Unprofessional impression: Not only, but especially during first visits, an improvised reception can make a negative impression, for example, if no contact person has been informed or a name tag is missing.
- High effort: Reception teams have to take care of registration, ID cards, directions, and notifying the host, often simultaneously and under time pressure. With higher visitor numbers, this is sometimes almost impossible to manage. And even when it is, it is not error-free.
The traditional reception desk comes under pressure when visitor numbers increase or new locations, new working models, or external service providers are added. The limitations of manual processes become apparent at this point at the latest and become a noticeable burden in everyday work.
Security and data protection in visitor management
Security, data protection, and user-friendliness are often difficult to reconcile. This is particularly due to the high demands placed on them. The entire process should be as convenient as possible for visitors, while at the same time fully protecting their data. For the company, the effort involved in visitor management should be minimal, but the level of professionalism displayed should be as high as possible.
- User experience (UX): The reception area is the first point of contact with the company. A digital check-in, clear signage, and a prepared host ensure a smooth process and avoid unnecessary waiting times or confusion.
- Access control: Guests should only be granted access where they are authorized, such as the meeting room, not the server room. In many companies, this means temporary authorizations, digital door systems, or approvals via the visitor system. Without such a system, it is often unclear who is where at any given time.
- General data protection: Visitors can see each other's data; data is not deleted properly. This can always have consequences, not only in particularly sensitive institutions such as research or administration.
- GDPR compliance: Companies must be able to prove what data they collect, for what purpose, how long it is stored, and who has access to it. A digital system can help here by automatically enforcing deletion deadlines and fulfilling information obligations in a structured manner.
In everyday work, it is often precisely this balancing act that poses a challenge: a process that is secure, legally compliant, and pleasant for visitors without overburdening the reception team.
{{cta}}
What types of visitor management systems are available?
a) Old-school visitor management
Traditional, but very outdated, visitor management relies on pen and paper. In principle, this can be used to gather information and get an overview, but only on one condition: the visitor has provided their correct name and has reasonably legible handwriting. Apart from that, filling out a paper form takes time and leads to waiting times at reception.
b) On-site software
A software solution installed on the PCs at reception makes work easier than visitor management with pen and paper. However, typical problems include a lack of synchronization of data, appointments, and other entries, as well as the isolation of the software. The team calendar and internal attendance overviews are not linked to it. From a technical standpoint, manual updates of the local software are an additional task.
c) Cloud-based management system
Cloud software is always up to date and data is synchronized across the company. This means that colleagues at reception can be confident that they are working with the right information. Another major advantage of a cloud-based visitor management system is the ability to integrate it with other platforms. This allows calendars and room bookings to be linked.
Examples of visitor management and best practices
The most important requirements for visitor management sometimes vary between different companies, institutions, and organizations.
Companies with high visitor traffic
Multiple guests at the same time, meetings in different buildings, external service providers on site: Digital check-in systems have proven their worth here, enabling quick visitor registration, often in multiple languages and without direct assistance from employees. The host is automatically informed and the visitor receives access to predefined areas via a badge or QR code. This reduces waiting times at reception.
Public institutions and authorities
Here, data protection and traceability are paramount. Visiting times, contact persons, and rooms must be precisely documented. Digital visitor lists help to reliably implement these requirements.
Shared offices and coworking spaces
Changing users, different companies, a high degree of flexibility: Centralized visitor management creates transparency about who is receiving which guests and when, and enables easy integration with room and access management. This is crucial for security and clarity, especially with teams that change daily.
Visitor management for desk sharing and flexible working
Hybrid working models, changing occupancy, shared desks: the way we work is changing, and with it the requirements for visitor management. As soon as the office concept no longer functions in the traditional way, structures are needed that:
- work even without a permanent reception staff,
- can handle spontaneous visits,
- are linked to room and workstation booking,
- manage visitor data centrally – across locations and in real time.
Structures created in-house can rarely meet these requirements. Tailored software is more reliable and significantly easier to use.
{{hint-box}}
Software for visitor management
There are many individual software solutions that only address one aspect of the overall problem. If you try to combine software of this kind into a functioning system on your own, you will usually quickly reach its limits. When making your selection, therefore, make sure that the software covers all your requirements as far as possible. Examples of important software functions in visitor management:
- Advance registration and sending invitations: Visitors can be registered in advance and automatically receive an invitation with all relevant information, including a QR code or link for check-in. This reduces the workload at reception and ensures that guests are well prepared.
- Self check-in on site: Visitors can register themselves using a tablet or terminal. Depending on your requirements, information such as name, company, reason for visit or safety instructions can be recorded.
- Automatic ID printing: After check-in, a visitor badge with name, company or photo can be generated immediately. This ensures clear identification in the building and visually supports security concepts.
- Notification to the host: As soon as a guest arrives, the responsible contact person is automatically informed: by email, messaging system, or in the calendar.
- Overview of all guests: Reception, security, or facility management can see at any time who is in the building, where they are, and for what purpose. This is not only relevant for evacuations, but also for data protection and compliance.
- GDPR-compliant data handling: Visitor data can be deleted or archived on a time-controlled basis, access can be logged, and inquiries can be answered.
- Integration with existing systems: It makes sense to link visitor management with other elements of everyday work, such as room or workstation booking, access systems, or calendar services.
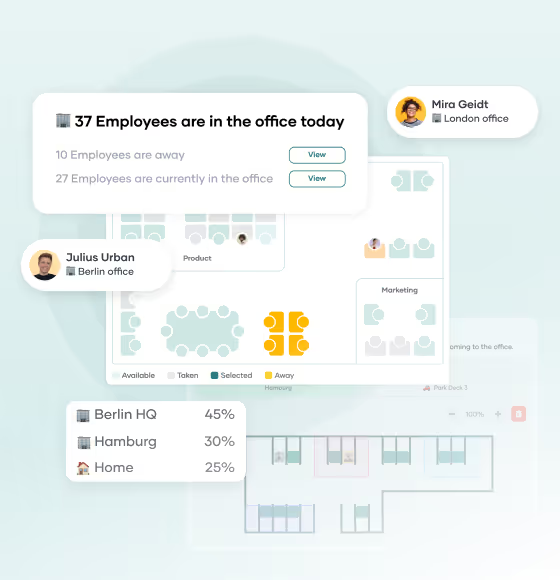
PULT provides all visitor management functions in one system: from pre-registration with a QR code and self-check-in at reception to automatic ID printing. The right employee is notified immediately, visitor data is documented in accordance with GDPR, and security officers can see who is in the building at any time.

What makes PULT special: Visitor management is directly linked to the work and parking space booking functions. This means your team has everything in one place and doesn't have to switch between different software. The same applies to the calendars used: bookings can be made directly from Outlook or Google Calendar. A new feature is 0-click check-in via Wi-Fi, which means your employees no longer have to actively log in and you can still see who is registered.
Visitor management – Frequently asked questions and answers
How does visitor management differ from traditional reception management?
Reception management usually refers to the physical greeting and assistance of guests. Visitor management goes beyond this: it encompasses all processes related to registration, access control, documentation, and follow-up.
What do I need to bear in mind when handling visitor data under the GDPR?
Visitor data is considered personal data. It may only be collected for a clearly defined purpose, must be stored securely, and deleted after a specified period of time.
Do I need my own IT department for visitor management?
No, PULT is cloud-based and does not require any local IT infrastructure, i.e., no dedicated servers or high-performance hardware. The software can be opened in any modern browser. No new hardware is required for 0-click login either: PULT Wifi uses the existing Wi-Fi network.
Can I manage service providers and tradespeople via visitor management?
Predefined check-in processes can be stored for external visitors, including safety instructions, ID printing, and temporary access authorization.
A new hybrid workplace experience is coming. Start Now. 🎉





















.avif)